A technique of enhancing bring-your-possess-gadget (BYOD) safety is by demanding staff members who use private units to set up protection software program to entry corporate networks, Hence maximizing centralized Command around and visibility into knowledge access and movement.
Rely upon IBM Support for Hyperledger Material As you create new and Highly developed business blockchain methods, Hyperledger Cloth open-supply code could be your Software of preference and you’ll want the most beneficial “satisfaction” assistance.
Extremely comprehensive research is a necessity — Among the many plethora of available alternatives, comparatively couple of right now are definitely enterprise-quality with correct stability ranges.
For the most basic stage, all SIEM answers conduct some volume of info aggregation, consolidation and sorting features to establish threats and adhere to data compliance necessities. While some answers vary in capability, most supply the exact same Main list of features:
Should you have followed cryptocurrencies considering the fact that their emergence (connection resides exterior ibm.com) in 2009 or have not too long ago caught on to the trend that has a fascination in Dogecoin, it’s essential to achieve an comprehension of their worth and what will make this digital asset something of worth as we transfer to an business centered all over decentralized finance.
Menace detection and reaction options Elevate your security with our Leading suite of copyright news and trends danger detection and reaction remedies.
You’re in all probability asking you; but why now? Bitcoin has been around since 2009. What’s so various this time? Perfectly, the main difference is regulators are starting to acquire discover and weigh in, offering fintechs, enterprises, banking institutions and Other people the guardrails within which to work.
IBM LinuxONE Emperor 4 A hugely protected, scalable server platform that can assist you achieve reduced Electrical power expenses in addition to a smaller sized carbon footprint.
Auditing: Interior audits assistance corporations Examine the performance of DAM and determine regions of enhancement. Similarly, regulatory bodies can audit a DAM Remedy to make certain a company’s engineering and processes comply with regulations. Both of those different types of audits occur routinely in very regulated industries like finance and healthcare.
Cryptocurrencies undoubtedly are a kind of payment which can be exchanged on line for products and providers. Many firms have issued their unique currencies, usually called tokens, and these is often traded specifically for the good or services that the corporation provides.
Investigate data safety expert services Take the following action Secure your information throughout its lifecycle with IBM Guardium. Protected critical business facts from both of those present and rising challenges, wherever it lives.
Remodel your workforce into “human firewalls”. Instructing them the value of great stability procedures and password hygiene and coaching them to recognize social engineering assaults is often very important in safeguarding your details.
Layout and implement your predefined knowledge correlation principles throughout all methods and networks, which include any cloud deployments.
However, we aren't only in this article to discuss the hoopla. We're here to handle how your organization can leverage digital assets and what developments are already designed over the last four yrs that leads us to feel now's the correct time.
 Michael Bower Then & Now!
Michael Bower Then & Now! Patrick Renna Then & Now!
Patrick Renna Then & Now!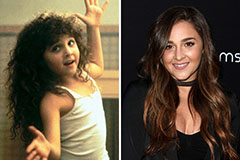 Alisan Porter Then & Now!
Alisan Porter Then & Now! Hailie Jade Scott Mathers Then & Now!
Hailie Jade Scott Mathers Then & Now! Lacey Chabert Then & Now!
Lacey Chabert Then & Now!